Cybersecurity crimes and data breaches are on the rise, and it is estimated that these crimes will cost $6 Trillion annually by 2021. Small to medium-sized businesses (SMBs) are more likely to fall victim. Oftentimes, SMBs don’t think they are large enough to be targets and lack the proper technology and processes to protect their network. In fact, 87 percent of SMBs surveyed by Symantec’s Security Threat Report said they didn’t feel like they were at risk for a breach.
When confronted with the daunting task of developing a cybersecurity strategy, many IT, security, and compliance leaders are not sure where to begin. This is understandable as figure 1. shows that there are many moving parts. Taking a framework approach to risk management offers a structured way to identify, protect, detect, respond, and recover from any security incident your business may face. Although there are many components to risk management, this guide will focus on data breaches in particular.
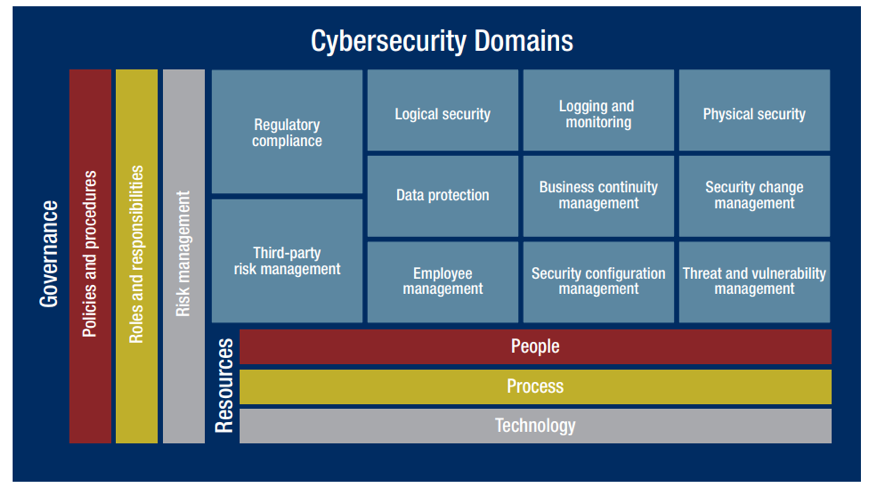
Figure 1: Cybersecurity Domains (Source: Crowe Analysis)
What is a Data Breach?
It is important to differentiate data breaches from other cybersecurity attacks. According to The Identity Theft Resource Center, a data breach is “an incident in which an individual’s name, social security number, driver’s license number, medical record, or financial record is potentially put at risk because of exposure.” In short, it is an incident where information is taken or stolen from a system without the authorization of the owner.
What is the Impact of a Data Breach?
Although no two data breaches are the same, they all have negative consequences, ranging from legal fines to having to close your doors for good. For businesses where sensitive data is exposed, the result is broken customer trust, loss of existing or new business, and lawsuits that result in hefty fines.
The year 2019 is shaping up to be a landmark one for data breaches. It has seen over 3,800 breaches, totaling over a 50 percent increase across the last four years, according to a report published by Risk Based Security.
The average cost of a data breach in the U.S. according to The Ponemon Institute is $8.19 million. The United States currently has the highest average cost in the world. These numbers may seem excessive to you, but you must consider both the direct and indirect costs associated with a breach. For instance, post-data breach response requires help desk activities, special investigations, regulatory mandates, and legal assistance. Once you survive that phase, you must then calculate any downtime that impacted operations and sales, loss of customer accounts due to reputational harm, or even loss of your entire business in some cases.
Types of Data Breaches
What are the most common types of data breaches? You need to understand each type to form a comprehensive plan for mitigation and remediation. If a breach does occur, how you contain its impact?
There are many types of breaches. Some are a result of employee error within an organization, and others are targeted attacks from external sources. Most breaches fall under these categories:
1. Hacks
Hacking, or malicious attacks have accounted for over 51 percent of data breaches in 2019. This includes attempts of phishing, spear phishing, ransomware, and skimming.
Traditional phishing is characterized by an email from a perpetrator. Those who receive the email assume the communication is from a trusted source, like a bank. The email often will guide the reader to click on a link to a malicious website. If the receiver clicks on the link, the hacker can infiltrate the user’s computer and steal their username and password.
Spear phishing is more targeted. Emails are sent to fewer but highly researched individuals or organizations. The attacker creates a customized message that appears credible so that the victim will unsuspectingly divulge critical information. Companies are highly susceptible to these types of hacks.
Ransomware, probably the most common type of hacking, uses crypto virology to take control of a victim’s data and block access to it until the victim pays a ransom.
Skimming, or card skimming, is the illegal copying of debit and credit cards. A store clerk might have a customer swipe a card more than once so that the magnetic strip can be copied, or an ATM might be rigged with a card skimmer.
Several well-known companies were targeted in attacks that proved extremely costly both in terms of revenue and reputation. Some of the most notable events include:
Equifax
Equifax, one of the three main US credit agencies, discovered a breach in July 2017. Because the data stolen included the social security, drivers’ license numbers, and other sensitive information of individuals, this could be the worst breach ever with 143 million consumers potentially affected. Hackers exploited a weak point that they discovered in the company’s system.
Gmail
In May 2017, a sophisticated phishing scam succeeded using a worm that posed as an email. The emails appeared to come from a trusted contact and enticed the victim to share a Google Doc via a link to a fake app, which took over the management of the Gmail account. Quick action by Gmail shut down the attack within an hour, but approximately 1 million users may have been affected.
2. Employee Error
Approximately 24 percent of all attacks are a result of employee error, according to the 2019 Cost of a Data Breach Report. These errors range in action, like not following proper security protocol or accidentally sharing sensitive information. Most errors happen without a malicious intent. Everyone is human, after all, and people make mistakes.
3. Accidental Exposure
In 7 percent of breaches, sensitive information is given up by accident. You’ll be surprised to learn it’s typically done by the company, however, not by an employee. Sometimes it can be hard to differentiate the two without proper research. For example, Saks 5th Avenue accidentally exposed customer information on their website via a plain text link. It was never determined if that was an employee error or just a glitch in the system.
4.Physical Theft
Theft of equipment or documents is another way that data breaches occur. This is a less subtle method of data breach because someone would have to steal a server or documents from a company. No major company has reported physical theft in the past few years most likely due to cloud storage.
5. Third-party Subcontractors
According to a Price Waterhouse Coopers survey conducted among 10,000 executives in 127 countries, almost 70 percent of companies use cloud-based cybersecurity services. However, third-party providers can be a source of security breaches.
Thousands of HIPAA-protected medical records were exposed from Bronx Lebanon Hospital Center in a data breach. A Rsync backup server hosted by a third party, iHealth, was misconfigured. In a separate incident in Maine, the names, addresses, and social security numbers of parents who received foster care benefits were inadvertently posted to a public website by a third-party contractor as part of a technology upgrade.
While the breaches did not happen directly to the companies, their customers were still impacted.
Prevention is Key
Breach prevention in the digital age requires advanced technology solutions such as network firewalls, file and hardware-based encryption, backup, malware protection, intrusion detection and protection, vulnerability scanning, and log management. It is also critical that your company has a proactive approach to security and retains the most knowledgeable security team available. Additionally, there are basic security policies that need to be in place for the ultimate data breach protection.
Four Policies for Proactive IT Security
Compliance requirements state various policies that companies should follow, but they are often uncorrelated and confusing. The following areas are pillars of a robust information security strategy.
1.Risk Management
When it comes to data breach and security, risk management is paramount. Statistics show that 60 percent of companies that lose data in a disaster shut down within six months. All risks should be identified and assessed in terms of cost and prioritized according to operational criticality.
Once identified, the level of resources needed to mitigate each identified risk can be allocated according to priorities. This analysis will form the basis for all other security-related decisions.
2. Asset Classification
Classifying assets defines the appropriate level of protection that is necessary for that data set. It will determine the cost of securing assets based on their value, the impact they have on the organization and its reputation, along with business opportunities that may be lost if the assets are gone. Classifying assets is prioritizing to determine which ones to protect first.
3.Information Systems Security
The Information Systems Security Policy defines which security controls should be executed for various information systems such as physical security, access management, and network security. The policy should be updated as new risks arise and technology is updated.
4. Information Systems Assessment and Authorization
The Information Systems Assessment and Authorization Policy is key to securing operations. This policy ensures that any new systems adopted are properly protected. It also requires all users to understand the defined standards and any deviation from those standards.
This policy should provide transparency and clarify who is responsible and how individuals will be held accountable for certain operations. The Information Systems Assessment and Authorization Policy links the three previous policies.
Developing these policies are exemplary of the Deming Cycle improvement process – plan, do, check, and act—which is a proven strategy for operational success.
How to Prevent Data Breaches
Companies who experienced breaches in the past skimped on encrypted storage and multi-factor authentication security measures to save time and increase productivity. The breach that affected Deloitte is a prime example. Their emails did not use encryption, the compromised administrator account was not protected by two-factor authentication and required only one password.
Round-the-clock, real-time monitoring is essential to preventing data breaches. Companies can only prevent data breaches if they have visibility into their environment. Outsourcing to a network security operations center to monitor activity 24/7/365 can be a good option, along with automated intrusion detection and prevention solutions. Tools, like a security information and event management platform (SIEM) provides actionable insights from advanced analytics and data forensics to mitigate risks and speed up your incident response.
SIEM systems consolidate logs from devices throughout your network to detect patterns in data over time; this intelligence allows you categorize issues according to their severity, so you can prioritize actions and make informed security decisions.
Employee expertise is vital, and security personnel should receive regular training so that they are aware of policies, expectations, and data security standards. As IT technology advances, so too should employee training so that staff are equipped with the latest tools and know how to apply them. Training is an investment that will pay dividends in the end.
Mitigating and Responding to a Security Breach
If a breach happens, there are certain steps that can mitigate and contain an incident. In the past we have seen several major companies including Yahoo and Uber try to conceal the depth of a breach. Companies must do everything in their power to protect customers and shareholders and be transparent about their efforts to build trust.
After a breach, a company should stem the flow and stop additional data loss by identifying vulnerabilities and fixing them.
Organize an expert response team
A response team should include forensic, legal, IT, HR, operations, communications, investor relations staff, and management experts. This team will be in charge of dealing with the aftermath of a breach in all aspects of your business.
Secure the physical area
Stemming the loss requires securing the physical area, as well as, the systems. Equipment should be taken offline or replaced (depending on the situation), access to your logical and physical environment should be monitored and frozen as necessary, and passwords and access codes for authorized users should be updated.
Calling on a world-class colocation provider to host your critical IT systems is the ultimate solution. That way your systems will always have the highest level of security, and you never have to take anything offline. LightEdge’s colocation services have a 100 percent uptime guarantee.
Check websites and online sources
Any misplaced information should be removed from public sources. Internet search engines can cache information, but you can directly contact a search engine to make sure they do not archive personal information. Other websites should be contacted and asked to remove any exposed data that they may have obtained from a compromised site.
Remove vulnerabilities
Check the network segmentation with forensic experts and see who gained access to what using the data from your SIEM agents and logs, and you may uncover the source of the issue. Investigate whether or not the proper procedures and technology were used and review your access logs for clues.
When identifying vulnerabilities, consider that they may originate from your third-party providers. Verify which data, applications, and systems were compromised prior to acting, and determine the number of individuals affected. Next, you will want to contact stakeholders to let them know a security incident has occurred and what steps you’re taking to recover.
Create a communications plan
Now is the time for transparency and communications both internally and externally. Companies that try to bury the extent of their breach, like Uber, often experience much worse consequences in customer backlash. Consider all stakeholders in the plan, including business partners, investors, employees, and customers.
Deliver a clear statement that is open and thorough without divulging information that could add risk. Organizations should report all data breaches to law enforcement and follow other state and federal legal requirements, including compliance mandates.
The Federal Trade Commission offers a detailed guide on how to mitigate a security breach including a model letter to send to customers and stakeholders.
How LightEdge Can Help
The best way to handle a data breach is to prevent it, but this is not always possible. LightEdge’s highly trained compliance and security experts take the guesswork out of keeping your business protected. Trust our expertise to ensure you are covered through our security and compliance services, including risk management, information security, audit preparedness, and support.
As a top-tier colocation services provider, we provide a high level of availability and reliability through secure, certified data centers and dedicated staff onsite. Our customized and scalable services give you the control, whether you need a colocation rack, cage, or custom suite now or in the future.
With geographically dispersed facilities across all of the US power grids, our data centers are the heart of our operation and yours. We have a wide range of colocation and disaster recovery solutions delivering advanced shared infrastructure designed to enable operational and financial efficiency, reducing the burden on your IT staff.
Customers turn to LightEdge to reduce risk of non-compliance, scale security, and for the predictably and cost-effectiveness. LightEdge provides customers with an extended team of experienced engineers and helps to focus resources on agility and differentiation. Are you curious how your current provider stacks up? Our security experts will provide a free security assessment to see how you measure up against the latest compliance and security standards. No risk, no commitment. Contact us today to get your free security assessment.
Related Posts:
- Why Insider Threats Are The Biggest Danger To Your Data
- Top Network Security Threats And How To Prevent Them
- Cybersecurity Break Through Infographic
- Your Business Needs A Cybersecurity Break Through
- The Future Of IT Security: What To Know And How To Survive
- Here’s How To Develop A Cybersecurity Recovery Plan
- What Is Disaster Recovery As A Service (DRaaS)?
- How To Determine If Your Business Is PCI Compliant
- What All Healthcare Companies Need To Know About HIPAA Compliance
- PCI DSS Cloud Compliance: Your Guide to a Smooth Cloud Migration
- 6 Best Practices for Data Security in the Cloud Infographic
- The Best of Both Worlds: Colocation and PCI DSS Compliance
- Ultimate Guide to a Highly Compliant Cloud Environment




